In this writeup, we’re going to set up an IPSec VPN between Juniper SRX and MikroTik RouterOS. To keep the Phase 1 tunnel simple, we’ll use IKE version 2 with pre-shared keys for authentication. RouterOS doesn’t yet support route-based Phase 2 tunnels, so we’ll configure policy-based on the RouterOS side, but keep the SRX side route-based so we can see how they interplay. If there’s enough interest in this content, I can turn this writeup into a video.
Topology
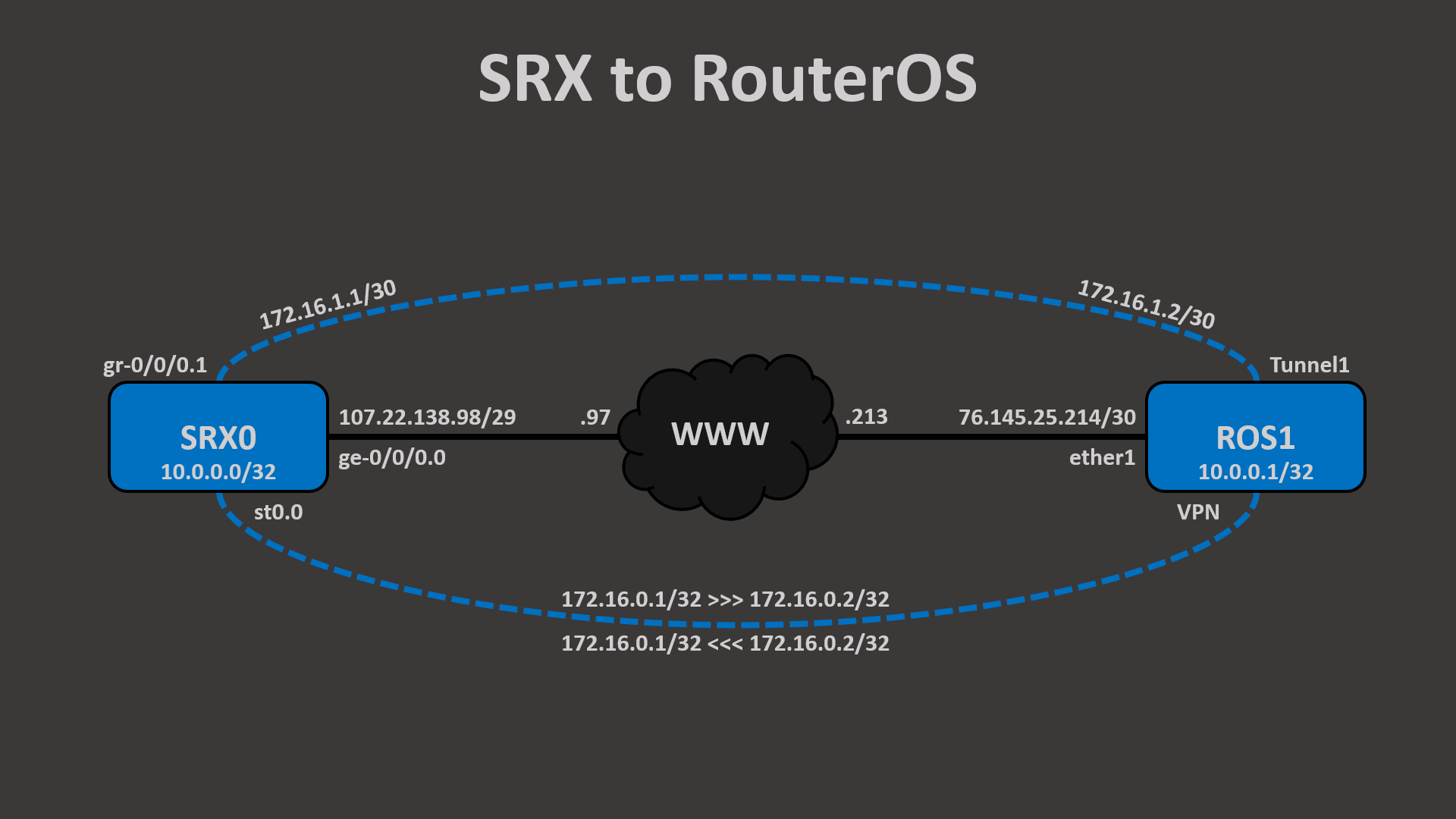
SRX
On the SRX side, our configuration is going to look similar to previous labs. We start with IKE, configuring the phase 1 tunnel settings under proposals, the pre-shared key under policy, and the peer specific settings, such as IP and identity, under gateway. We also need the hostname, of course!
set system host-name SRX0 set security ike proposal IKE_PROP authentication-method pre-shared-keys set security ike proposal IKE_PROP dh-group group14 set security ike proposal IKE_PROP authentication-algorithm sha-256 set security ike proposal IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal IKE_PROP lifetime-seconds 86400 set security ike policy IKE_POLI proposals IKE_PROP set security ike policy IKE_POLI pre-shared-key ascii-text thisisanSRXtoROSlab set security ike gateway ROS1 ike-policy IKE_POLI set security ike gateway ROS1 address 76.145.25.214 set security ike gateway ROS1 local-identity hostname SRX0 set security ike gateway ROS1 remote-identity hostname ROS1 set security ike gateway ROS1 external-interface ge-0/0/0.0 set security ike gateway ROS1 version v2-only
Next is IPSec, where we configure the phase 2 tunnel settings under proposals, the PFS under policy, and the tunnel specific settings, such as the interface, under gateway. Notice how we also configure the local and remote proxy-identities. Because RouterOS only supports policy-based IPSec, the proxy-identities (a.k.a. traffic-selectors) are necessary so that the SRX will agree with the RouterOS on which traffic is support to traverse the IPSec VPN.
set security ipsec proposal IPSEC_PROP protocol esp set security ipsec proposal IPSEC_PROP authentication-algorithm hmac-sha-256-128 set security ipsec proposal IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec proposal IPSEC_PROP lifetime-seconds 28800 set security ipsec policy IPSEC_POLI perfect-forward-secrecy keys group14 set security ipsec policy IPSEC_POLI proposals IPSEC_PROP set security ipsec vpn ROS1 bind-interface st0.0 set security ipsec vpn ROS1 df-bit copy set security ipsec vpn ROS1 ike gateway ROS1 set security ipsec vpn ROS1 ike proxy-identity local 172.16.0.1/32 set security ipsec vpn ROS1 ike proxy-identity remote 172.16.0.2/32 set security ipsec vpn ROS1 ike ipsec-policy IPSEC_POLI
Now that we have phase 1 and 2 configured, let’s finish up our other security configurations, namely the TCP MSS clamping, the security policy for intra-zone traffic, and the security zone definitions.
set security flow tcp-mss gre-in mss 1360 set security flow tcp-mss gre-out mss 1360 set security policies from-zone CORP to-zone CORP policy Permit_Any match source-address any set security policies from-zone CORP to-zone CORP policy Permit_Any match destination-address any set security policies from-zone CORP to-zone CORP policy Permit_Any match application any set security policies from-zone CORP to-zone CORP policy Permit_Any then permit set security zones security-zone WWW host-inbound-traffic system-services ping set security zones security-zone WWW host-inbound-traffic system-services ike set security zones security-zone WWW interfaces ge-0/0/0.0 set security zones security-zone CORP host-inbound-traffic system-services all set security zones security-zone CORP host-inbound-traffic protocols all set security zones security-zone CORP interfaces lo0.0 set security zones security-zone CORP interfaces st0.0 set security zones security-zone CORP interfaces gr-0/0/0.1
Ok, so with security done, let’s get the interfaces configured. We have the WWW interface which anchors the IKE and IPSec, the loopback interface which we’ll OSPF advertise over the VPN, and the IPSec tunnel interface. Because RouterOS is going to be policy-based, we can’t simply OSPF peer over the IPSec interface, and so we need a GRE tunnel interface. The IPSec tunnel interface will only allow the traffic defined by the proxy-identities, and that is what we’ll be using for the GRE tunnel source and destination. By giving st0.1 an address of 172.16.0.1/30, we’re telling the SRX that 0.2 is reachable via the st0.1 interface. We could also accomplish this by removing the 0.1/30 address, configuring it on lo0.0, and instead, using a static route to point to 0.2 via st0.1. Either way works.
set interfaces ge-0/0/0 description WWW set interfaces ge-0/0/0 unit 0 family inet address 107.22.138.98/29 set interfaces gr-0/0/0 unit 1 description ROS1 set interfaces gr-0/0/0 unit 1 tunnel source 172.16.0.1 set interfaces gr-0/0/0 unit 1 tunnel destination 172.16.0.2 set interfaces gr-0/0/0 unit 1 family inet mtu 1400 set interfaces gr-0/0/0 unit 1 family inet address 172.16.1.1/30 set interfaces lo0 description Loopback set interfaces lo0 unit 0 family inet address 10.0.0.0/32 set interfaces st0 unit 0 description ROS1 set interfaces st0 unit 0 family inet address 172.16.0.1/30
We’ll wrap up with our protocols and routing-options. Because the RouterOS always sends GRE tunnel keepalives, we’ll turn those on here on the SRX for sanity’s sake, although you could run them in just one direction. We’ll also run OSPF as passive on our loopback and regular on our GRE tunnel. Finally, we’ll make sure our default static route is pointing to our ISP and that our router ID is set for OSPF.
set protocols oam gre-tunnel interface gr-0/0/0 keepalive-time 5 set protocols oam gre-tunnel interface gr-0/0/0 hold-time 15 set protocols ospf area 0.0.0.0 interface lo0.0 passive set protocols ospf area 0.0.0.0 interface gr-0/0/0.1 set routing-options static route 0.0.0.0/0 next-hop 107.22.138.97 set routing-options static route 0.0.0.0/0 no-readvertise set routing-options router-id 10.0.0.0
RouterOS
On the RouterOS side, our configuration isn’t a candidate that’s committed at once, like with SRX, but every command is executed as it’s entered, like with Cisco. So the order that we enter the commands matter since some are dependent on the others. We’ll start with configuring our hostname, loopback interface, and WWW interface. Notice how we’re using a bridge interface as our loopback and our it has two IPs: our 10.0.0.1 that we’ll advertise to SRX0 over the GRE via OSPF, and 172.16.0.2 which is the GRE tunnel anchor. Since RouterOS doesn’t support route-based IPSec yet, we have no IPSec VPN interface to configure 172.16.0.2 on.
/system identity set name=ROS1 /interface bridge add mtu=1500 name=Loopback0 protocol-mode=none /ip address add address=10.0.0.1 interface=Loopback0 network=10.0.0.1 /ip address add address=172.16.0.2 interface=Loopback0 network=172.16.0.2 /interface ethernet set [ find default-name=ether1 ] comment=WWW /ip address add address=76.145.25.214/30 interface=ether1 network=76.145.25.212 /ip route add distance=1 gateway=76.145.25.213 /interface gre add dont-fragment=inherit keepalive=5s,2 local-address=172.16.0.2 mtu=1400 name=Tunnel1 remote-address=172.16.0.1 /ip address add address=172.16.1.2/30 interface=Tunnel1 network=172.16.1.0
Next we’ll configure IKE, which RouterOS divides up into the Profile(phase 1 proposals), Peer, and Identity sections. Notice how I’m explicitly defining the IKE source port as 500(UDP). When I don’t do this, it keeps using 4500 even though there is no NAT detected and even with NAT-T disabled. I’m not sure if that is a bug or intention.
/ip ipsec profile add dh-group=modp2048 dpd-interval=disable-dpd enc-algorithm=aes-256 hash-algorithm=sha256 name=IKE_PROP /ip ipsec peer add address=107.22.138.98/32 exchange-mode=ike2 name=SRX0 port=500 profile=IKE_PROP /ip ipsec identity add my-id=fqdn:ROS1 peer=SRX0 remote-id=fqdn:SRX0 secret=thisisanSRXtoROSlab
After that, we’ll configure IPSec, which are split between Proposals(phase 2 proposals) and Policy. This is pretty straight forward for those familiar with policy-based VPN configurations of other vendors.
/ip ipsec proposal add auth-algorithms=sha256 enc-algorithms=aes-256-cbc lifetime=8h name=IPSEC_PROP pfs-group=modp2048 /ip ipsec policy add dst-address=172.16.0.1/32 peer=SRX0 proposal=IPSEC_PROP src-address=172.16.0.2/32 tunnel=yes
Finally, we’ll configure OSPF as passive on the loopback and p2p on the GRE tunnel.
/routing ospf instance set [ find default=yes ] router-id=10.0.0.1 /routing ospf interface add cost=1 interface=Loopback0 network-type=point-to-point passive=yes /routing ospf interface add cost=1 interface=Tunnel1 network-type=point-to-point /routing ospf network add area=backbone network=10.0.0.1/32 /routing ospf network add area=backbone network=172.16.1.0/30
And now for verification on RouterOS.
[admin@ROS1] > interface print Flags: D - dynamic, X - disabled, R - running, S - slave # NAME TYPE ACTUAL-MTU L2MTU MAX-L2MTU 0 R ;;; WWW ether1 ether 1500 1 R ether2 ether 1500 2 R ether3 ether 1500 3 R Loopback0 bridge 1500 65535 4 R Tunnel1 gre-tunnel 1400 65535 [admin@ROS1] > ip address print Flags: X - disabled, I - invalid, D - dynamic # ADDRESS NETWORK INTERFACE 0 10.0.0.1/32 10.0.0.1 Loopback0 1 172.16.0.2/32 172.16.0.2 Loopback0 2 76.145.25.214/30 76.145.25.212 ether1 3 172.16.1.2/30 172.16.1.0 Tunnel1 [admin@ROS1] > ip ipsec active-peers print detail Flags: R - responder, N - natt-peer 0 R id="SRX0" local-address=76.145.25.214 remote-address=107.22.138.98 state=established side=responder uptime=17m1s last-seen=17m1s ph2-total=1 [admin@ROS1] > ip ipsec installed-sa print Flags: H - hw-aead, A - AH, E - ESP 0 E spi=0xDA3EE15 src-address=107.22.138.98 dst-address=76.145.25.214 state=mature auth-algorithm=sha256 enc-algorithm=aes-cbc enc-key-size=256 auth-key="ad6c3223aad25e43e43340c883c6fadcdfadb30ba842682ea87a77f70f7826e2" enc-key="01dc8ac98b2383b46c998e71575e1cee24c8a8b743ec29b1a320ee2280772252" addtime=dec/04/2020 18:52:44 expires-in=7h42m41s add-lifetime=6h24m9s/8h12s current-bytes=35636 current-packets=547 replay=128 1 E spi=0xD146B053 src-address=76.145.25.214 dst-address=107.22.138.98 state=mature auth-algorithm=sha256 enc-algorithm=aes-cbc enc-key-size=256 auth-key="2243a6cd1cb97080fef2bb3575cbf300cedbbc46b484aad7b6bffb6406ccd576" enc-key="2d296a915b8625fa2cb8d046c53bf2fe9ce6035afe8a947d2287819ca0f1eb06" addtime=dec/04/2020 18:52:44 expires-in=7h42m41s add-lifetime=6h24m9s/8h12s current-bytes=31964 current-packets=527 replay=128 [admin@ROS1] > routing ospf neighbor print 0 instance=default router-id=10.0.0.0 address=172.16.1.1 interface=Tunnel1 priority=128 dr-address=0.0.0.0 backup-dr-address=0.0.0.0 state="Full" state-changes=5 ls-retransmits=0 ls-requests=0 db-summaries=0 adjacency=17m42s [admin@ROS1] > ip route print Flags: X - disabled, A - active, D - dynamic, C - connect, S - static, r - rip, b - bgp, o - ospf, m - mme, B - blackhole, U - unreachable, P - prohibit # DST-ADDRESS PREF-SRC GATEWAY DISTANCE 0 A S 0.0.0.0/0 76.145.25.213 1 1 ADo 10.0.0.0/32 172.16.1.1 110 2 ADC 10.0.0.1/32 10.0.0.1 Loopback0 0 3 ADC 76.145.25.212/30 76.145.25.214 ether1 0 4 ADC 172.16.0.2/32 172.16.0.2 Loopback0 0 5 ADC 172.16.1.0/30 172.16.1.2 Tunnel1 0 [admin@ROS1] > ping 10.0.0.0 src-address=10.0.0.1 count=5 size=1400 do-not-fragment SEQ HOST SIZE TTL TIME STATUS 0 10.0.0.0 1400 64 14ms 1 10.0.0.0 1400 64 8ms 2 10.0.0.0 1400 64 0ms 3 10.0.0.0 1400 64 0ms 4 10.0.0.0 1400 64 9ms sent=5 received=5 packet-loss=0% min-rtt=0ms avg-rtt=6ms max-rtt=14ms